Who Has Your Digital Fingerprint?
What is digital fingerprinting?
We know fingerprinting to be a method that identifies people by the palm-side patterns covering their fingertips.
Digital fingerprinting operates in a similar fashion, but rather than identifying a person, per se, these types of fingerprints use digital patterns, or settings, to identify an individual’s browser and/or device—computer, mobile phone, tablet, even TV.
Browser fingerprints are generated from browser settings/inputs, such as screen size, installed plugins/extensions, time zone, languages and fonts. A full list of these inputs can be found here.
Some of the more advanced browser fingerprinting methods include canvas and WebGL fingerprinting. Both of these special feature fingerprints are generated from the creation of images in the background of a user’s browser without the user knowing. How the browser creates these images is what defines the unique fingerprint. In other words, only a browser with settings XYZ can create image XYZ.
To prevent browser fingerprinting, many people think to use multiple browsers, and this was possible, for a time. Sadly though, not anymore. There now exists cross-browser fingerprinting. Yinzhi Cao, Assistant Professor in the Computer Science and Engineering Department at Lehigh University, along with students Song Li and Erik Wijmans, released a paper describing how cross-browser fingerprinting works.
The paper explains how code is implemented into websites and instructs browsers to pull information from operating-systems/device hardware, like graphics cards, CPUs and audio cards. In all, he utilized 29 features by writing scripts that force a user’s computer to run 36 tasks. Among these features were audio, keyboard, and even battery fingerprints, and when all 29 features were cross-referenced, he was able to uniquely identify a device with a 99.24% accuracy rate—improving upon the 90.84% accuracy rate of single-browser fingerprinting.
The source code for this cross-browser technique has been published on GitHub, making it open to the public.
The purpose of digital fingerprinting
Advertisers and marketers want to know what content people see along with when and where people see the content. They also want to analyze engagement with content over an extended period of time. From this information, advertisers and marketers are able to target their audiences more effectively.
To do this in the digital world, online tracking tools are implemented. The first of these online tracking tools to enter the scene were web cookies. It is important to understand the purpose of web cookies before diving into the purpose of fingerprinting.
 Brief explanation of how web cookies operate:
Brief explanation of how web cookies operate:
A website using cookies has special cookie scripts written into the source code of the website. The scripts tell a browser to make small text files on a user’s computer; it is these text files that are the actual web cookies.
If a script for Cookie WC is written into Website W’s source code, the Cookie WC text file will be stored on User U’s computer upon User U’s arrival to the site. Should User U leave the site but return another day, the browser will pull the Cookie WC text file from User U’s computer and send the information stored in Cookie WC back to Website W, thus enabling Website W to recognize the returning ID number of Cookie WC as User U.
Web cookies store information like location, preferred language and sometimes even personal details. It is up to the creator of the cookie to determine what information is collected, and it is up to the user to determine if personal information is given. Cookies also track a user’s session within a site (i.e. how the user arrives, how the user navigates, how much time the user spends on each page, etc.).
In the case of third-party advertisers, such as ad exchange companies like Google DoubleClick, AppNexus, Microsoft Media Network and OpenX, they install their own scripts in website source codes through the ads they display across sites.
Now, when User U visits Website W, third-party Ad Company A, has its own script for Cookie AC installed in Website W’s source code. User U’s computer will then store text files for both Cookie WC and Cookie AC. Cookie AC being completely separate from Website W.
If User U visits another site—Website Y—that also contains Ad Company A’s script for Cookie AC, User U’s computer will send the information and ID number of Cookie AC’s text file back to Ad Company A. Ad Company A is now able to recognize that User U visited both Website W and Website Y. This is how third-party advertisers recognize users across multiple sites along with multiple pages within a site.
Cookies stay on a users’ computers for a specified amount of time. This can be anywhere from one day to a month, even longer. From these web cookies, customer profiles are created, and unless personal information, such as an email address, is obtained, the ID number assigned to the cookie acts as the identification of the user within the customer database.
As more people become aware of online tracking, those who desire to browse the internet more freely tend to delete their cookies quite regularly. Some set up their browsers to remove cookies after each session and others use private windows, like Chrome’s Incognito, to prevent cookie tracking. This makes it difficult for third-party advertisers to see who is viewing their ads.
Enter in, fingerprinting. This technique of web tracking was created as a more permanent alternative to web cookies. Flash Cookies (Local Shared Objects or LSOs) and Ever Cookies were also created as alternatives to the standard cookie, but eventually browsers made it possible to prevent and remove these tricky cookies from users’ computers as well. A cross-browser fingerprint, however, cannot be removed nor easily prevented.
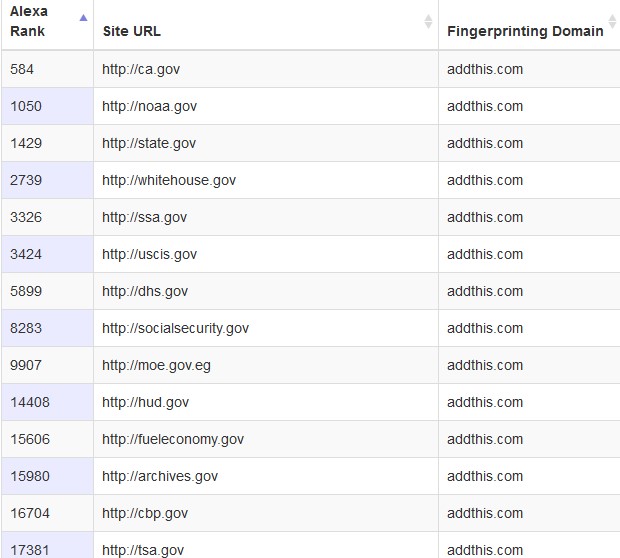
Browser fingerprinting came into the world around 2010, and since that time, the technique has been used among many websites. A 2014 study conducted by researchers at KU Leuven University (Belgium) and Princeton University found that more than 5.5% of the top 100,000 Alexa sites were using canvas fingerprinting.
Of these sites, 95% were using a script written by a company called AddThis. AddThis responded to the release of information in one of their blog posts, saying they were running an experiment and that the “data was never used for personalization or targeted advertising” nor did they identify individuals specifically. They also stated that they will notify users before commencing the tests going forward, implying users were not notified of the canvas fingerprinting experiment. To receive these notifications, however, people are required to subscribe to the AddThis email list—providing personal information. Should a user want to opt-out of AddThis tracking scripts, the user would need to allow a special AddThis “Do not Track” cookie to be created, and if the user clears his or her cookies, he or she becomes susceptible to tracking scripts again. This email-cookie combination also becomes a replacement to the fingerprinting.
AddThis stated that the experiment was only able to identify browsers with a 90% accuracy rate via canvas fingerprinting, which, in their opinion, was too low. With the newer cross-browser fingerprinting techniques, though, simple browser fingerprinting is old news. Websites that use the cross-browser technique identify entire devices, rather than a single browser, and have a higher accuracy rate, as mentioned above.
Who uses cross-browser fingerprinting?
Some companies, such as banks, claim to use fingerprinting on their websites for fraud prevention and safety. Banks want to recognize when their clients’ accounts are being accessed by unknown or suspicious devices. A device is considered suspicious when the device is difficult to fingerprint, so this is quite ironic.
Government sites are also known to use fingerprinting, most likely for the same reason as banks: security.
It’s hard to say which companies are using digital fingerprinting, as it’s typically not something a company openly declares. Güneş Acar, one of the lead researchers in the KU Leuven University (Belgium) and Princeton University paper mentioned above, also worked on the development of a program called FPDetective that crawled website homepages in 2013, looking for canvas fingerprinting scripts. Unfortunately though, it doesn’t seem there are any recent studies into what sites currently use cross-browser fingerprinting.
By installing a browser extension called Ghostery, you can see most every third-party script that is embedded in the source codes of the web pages you visit. This is the best way to figure out what businesses are collecting your information and how they do it.
 How to prevent digital fingerprinting
How to prevent digital fingerprinting
The best way to prevent browser fingerprinting is by using the Tor browser and its default settings. It is important to keep the browser’s settings as the default because even Tor has come under attack by trackers using the entry and exit points to Domain Name Servers (DNS) lookups.
The “Do not Track” setting of popular browsers is more of a joke and actually helps fingerprint you more successfully, so this technique should not be relied upon.
Here is a link that explains, in great detail, a variety of methods to help prevent digital fingerprinting: http://howagain.com/counter-device-fingerprinting/
It is important to note, though, browser extensions to prevent fingerprinting make a browser more unique and potentially easier to fingerprint. It’s like a Catch-22 situation.
Be aware
It is important for people to know who is tracking what online along with how and why; otherwise, users may wake up one day and find that privacy is no longer an option. The fight between tracker and tracking preventers will continue on, especially if real policy changes aren’t made in regards to how the online world is allowed to operate. Such changes won’t be made, though, if people don’t first make it an issue.
Further Reading:
Here is a link to the 2017 PhD Thesis paper of Güneş Acar that details his research in digital fingerprinting: https://www.esat.kuleuven.be/cosic/publications/thesis-289.pdf
Do you mind if your device is fingerprinted?
If you don’t mind, do you want to be made aware of when your device is fingerprinted, or is this also irrelevant to you?
Feel free to share your thoughts in the comment section below.